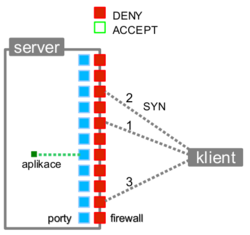
Figure 4 from Simple port knocking method: Against TCP replay attack and port scanning | Semantic Scholar
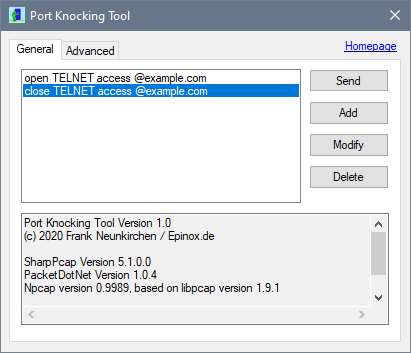
Port knocking, aprenda a melhorar as política de segurança de seu firewall Linux e Mikrotik - Remontti

Sniffing The Keys To The Server. Stealing Port Knock Sequences For… | by Vickie Li | InfoSec Write-ups

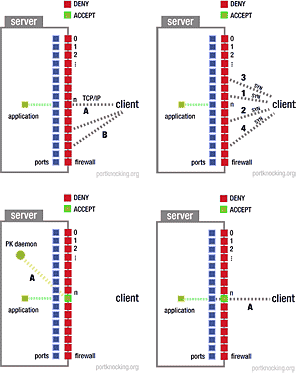
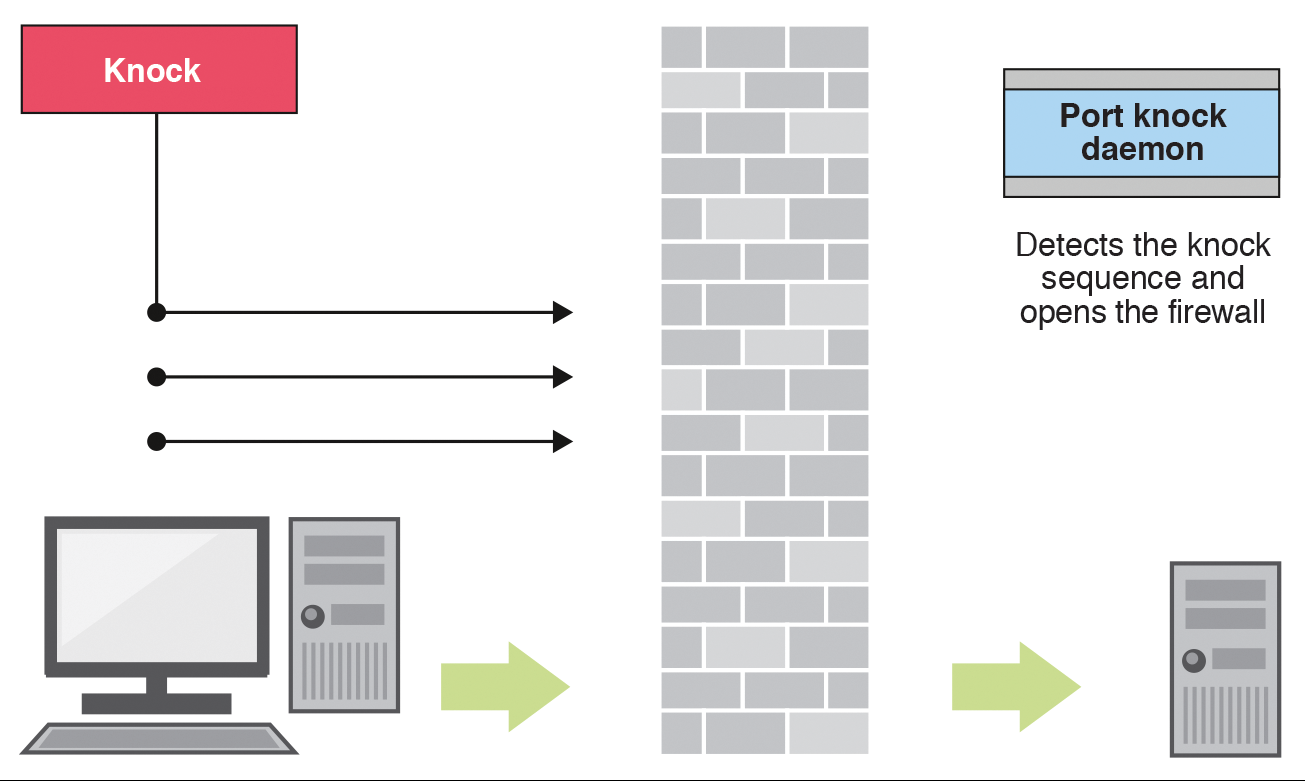
Port knocking example. The firewall is opened in response to a specific... | Download Scientific Diagram





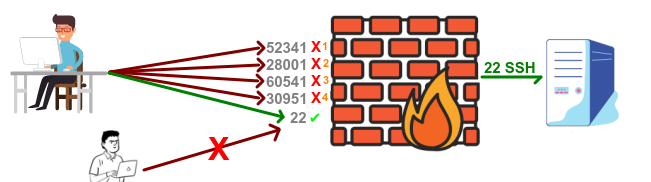
![EP.17] Protecting MikroTik Login with Port Knocking (MTCSE) - techblogclub - Medium EP.17] Protecting MikroTik Login with Port Knocking (MTCSE) - techblogclub - Medium](https://miro.medium.com/max/655/1*CwtTF6v5urUVPzPNKz-NxA.png)